Brief overview
On this page you can find projects from my channel, as well as featured software. Please credit Enderman/MalwareWatch and/or original authors if you plan to publicly share the information or showcase given software anywhere
on the Internet. Sharing is caring!
If you'd like to get your software project or an idea featured on my channel, contact us at [email protected]! Heads up: most of the suggestions are turned down,
since the quality bar is extremely high. Don't be disappointed if your project doesn't quite make it. Contact us only if you have something actually worthy to share - that will save a lot of time for us and strengthen your
chances of securing a spot here. Thanks in advance.
Submissions
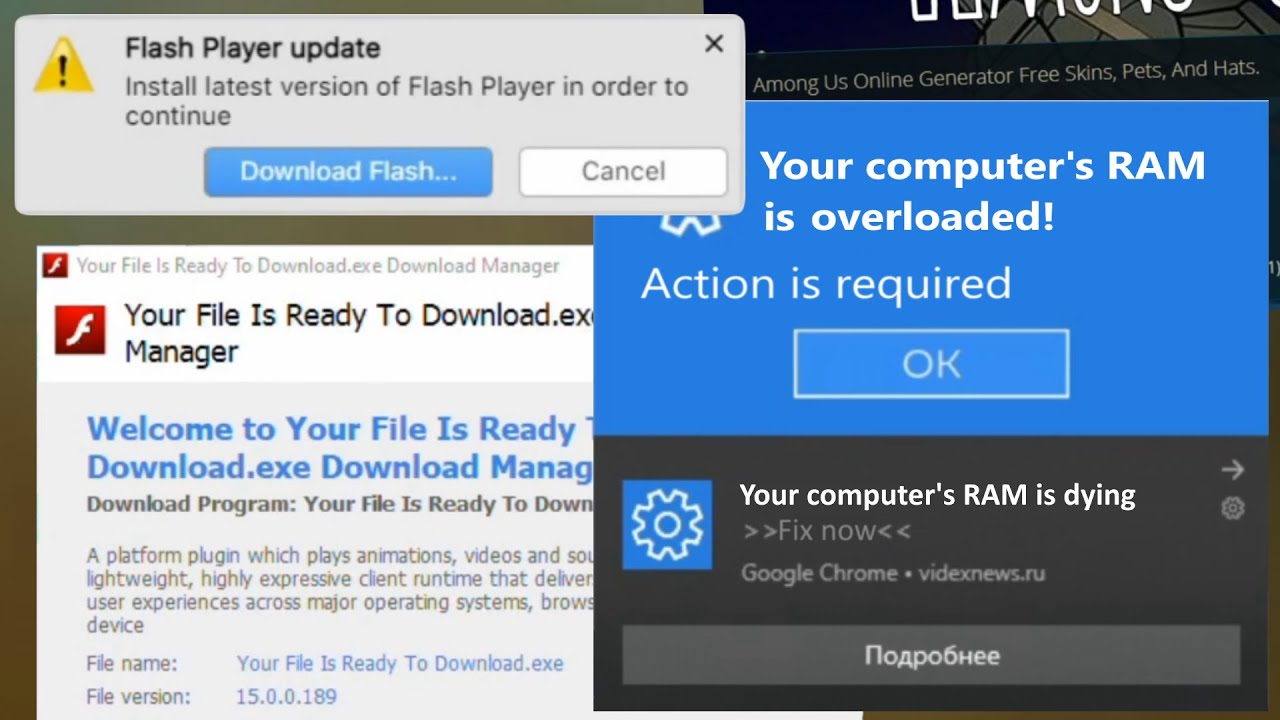
We will respond only to the best of the best submissions, we ignore intentionally garbage or common mainstream malware (e. g. GDI, BitBlt spam, MBR overwriters, forkbombs). The best types of submissions include but are not limited to:- HDD images of severely Adware-infected machines The best for comprehensive analysis
- Rogue Antimalware/FakeAV programs and collections The most valued
- Annoying PUPs
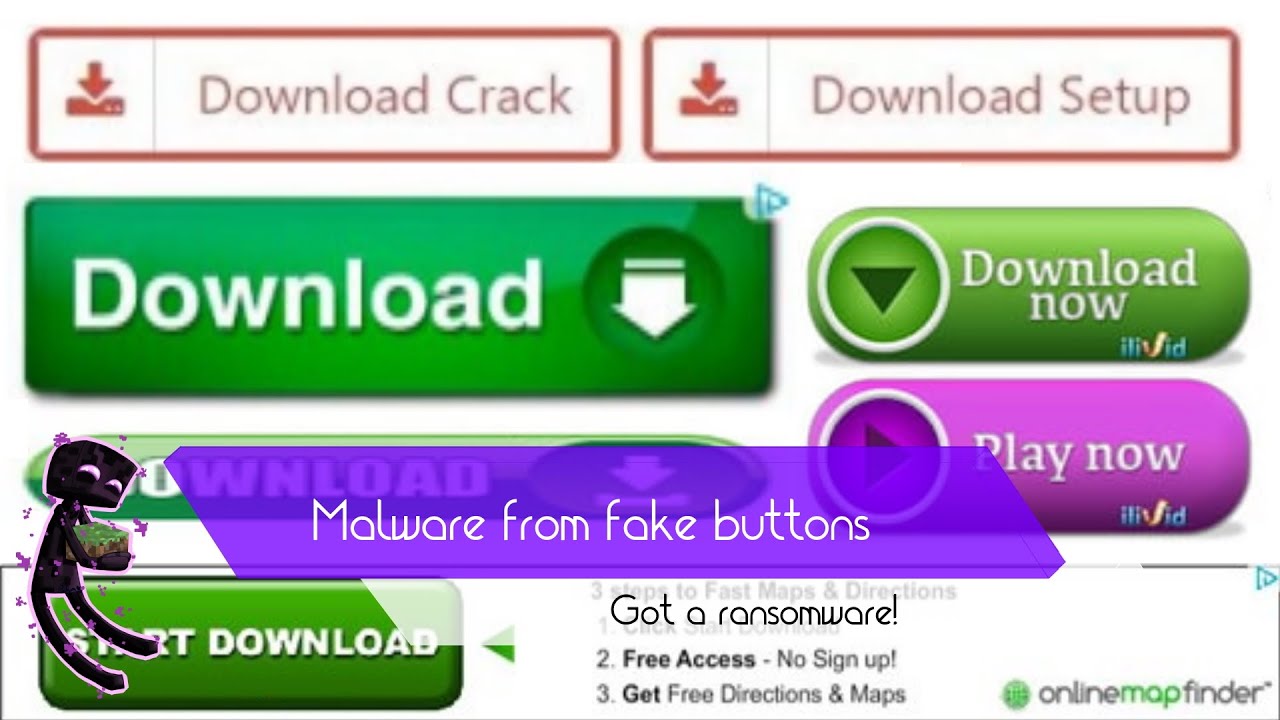
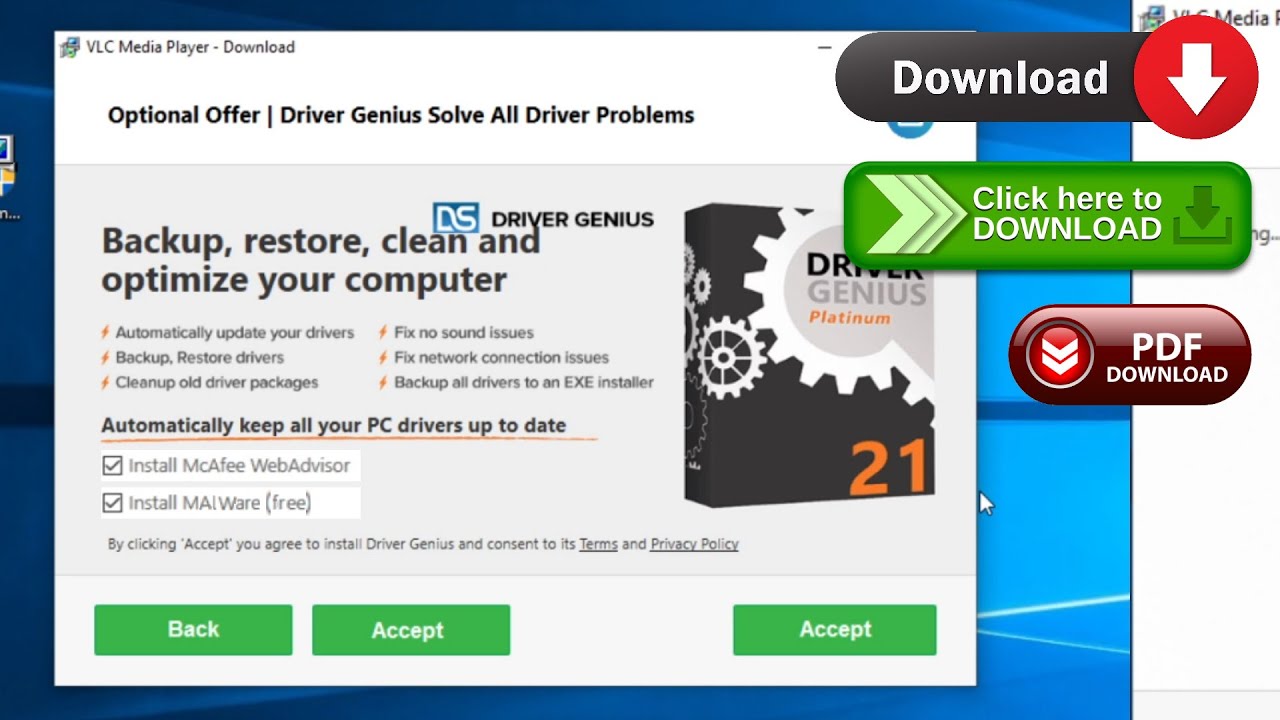
- Rare OpenCandy and/or fake installers with optional offers
- Adware modules & droppers
- Toolbars & docked browsers
- Browser link & start page modifiers
- Any fake or malicious Adobe Flash Player installer The rarest installers
Composing an e-mail
Already got something to share? That's great news! Let me show you where to begin. For convenience sake, I created a template. It's easy to compose and search for in the flood of messages in my inbox! Here are a few rules you might want to stick to:
- Title should contain the words "submission" in it. I check most of the e-mails, but "submission" is of way higher priority.
Got no idea what to call the e-mail? Type in Adware Submission. - In the e-mail itself, tell me where the file originated from. If its origin is some shady website, attach the link to it as well.
If you're sending a website submission, that's perfectly fine! Just link it, and that's it! - Optionally, attach a screenshot of it in action.
- Double-check you send the malware to a correct recepient - [email protected]
Examples
Here's an example of 2 well-composed e-mails, which I quickly located in my inbox, analyzed with almost no effort and responded to.
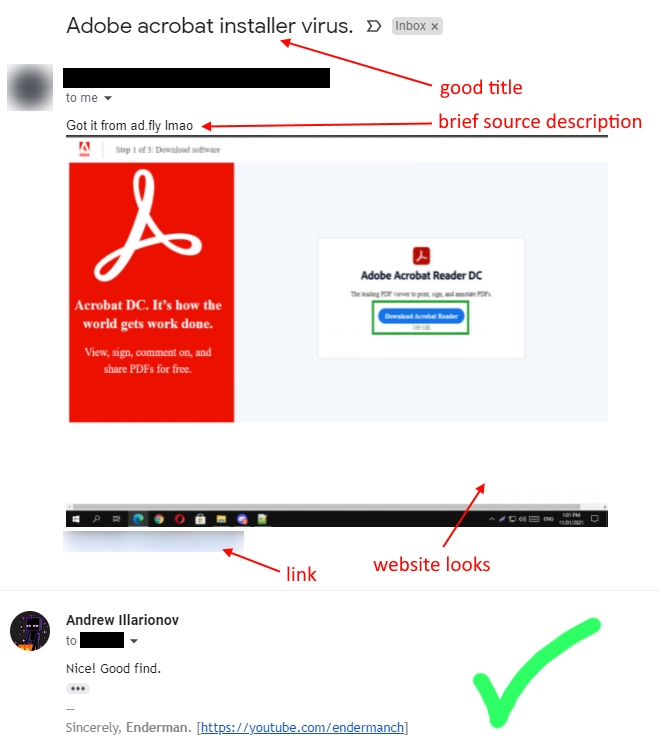
Successful transfer
This might get featured in a future video!
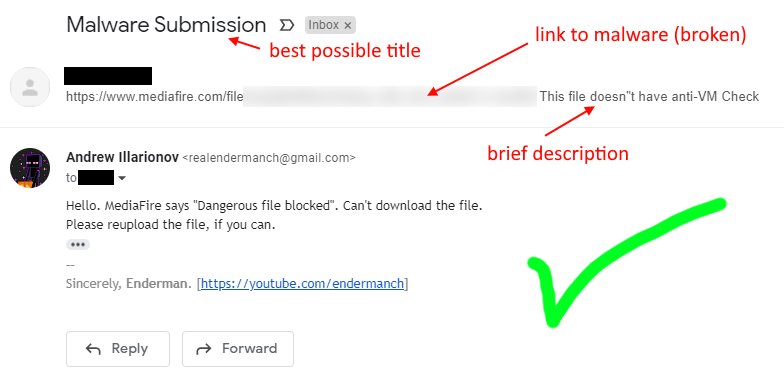
Failed transfer
I couldn't acquire the sample and explained the reason in a reply.